MAC address flooding is a great way to render a network useless. Basically, through MAC flooding, you can turn the network into a large hub. MAC flooding works by essentially allowing the switch ports to learn as many MAC addresses as they see on their ports, and if no limits on in place, can fill up the TCAM space on the switch. Once this happens, switches turn themselves into hubs, since they can’t store the MAC for the port. They need to send every packet out to every switch to try and get the packet delivered.
Macof is a member of the dsniff suit tool set and is mainly used to flood the switch on a local network with MAC addresses. Macof generates thousands of packets per second, and each packet is sent random source and destination IP addresses. A source and destination MAC address is also different for each Ethernet frame.
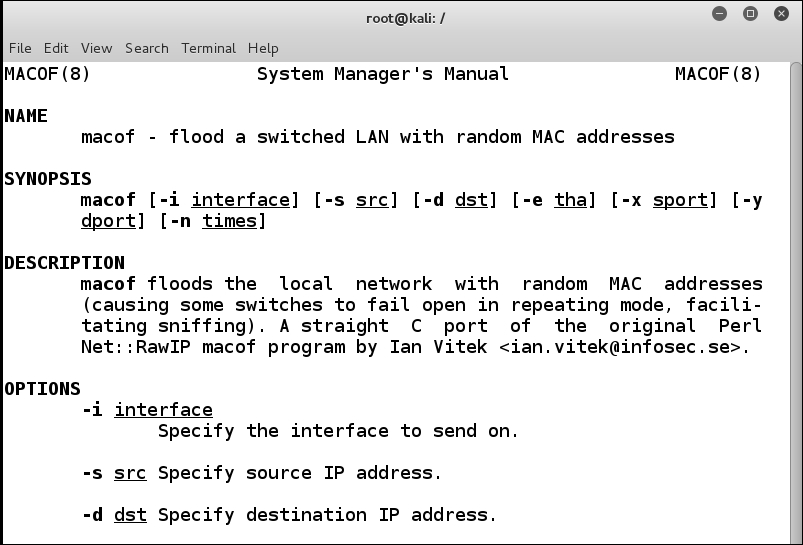
The syntax of macof is as follows. Check out the man page or –help to get a full description of the available options:
# macof [-i interface] [-s src] [-d dst] [-e tha] [-x sport] [-y dport] [-n times]
If you encounter below error:
macof: command not found
you may try installing below package as per your choice of distribution.
| Distribution | Command |
|---|---|
| Debian | apt-get install dsniff |
| Ubuntu | apt-get install dsniff |
| Arch Linux | pacman -S dsniff |
| Kali Linux | apt-get install dsniff |
| Fedora | dnf install dsniff |
| Raspbian | apt-get install dsniff |
Summary
MAC addresses are unique identifiers with two assigned parts—the OUI is assigned by IEEE, and the second 24 bits are assigned by the manufacturer. These addresses are stored in a table called the Content Addressable Memory (CAM). Attackers can exploit the CAM table to perform malicious activities. An attack called CAM overflow can be carried out. In other words, attackers overflow the CAM tables by exploiting the maximum limit of the CAM table size. There are many tools available, one of which is macof.