The GRUB bootloader stores the password in a plaintext file, so any encrypted form of the password is required. To generate an encrypted password we may use grub-crypt command. Until now we have used the command grub-md5-crypt. But now MD5 is widely-considered broken. grub-crypt uses SHA-256 or SHA-512 hashes, which are considered more secure. The general syntax/usage of the grub-crypt command is as shown below :
# grub-crypt --help Usage: grub-crypt [OPTION]... Encrypt a password. -h, --help Print this message and exit -v, --version Print the version information and exit --md5 Use MD5 to encrypt the password --sha-256 Use SHA-256 to encrypt the password --sha-512 Use SHA-512 to encrypt the password (default) Report bugs to [bug-grub@gnu.org]. EOF
Using SHA-265 or SHA-512 hashes
1. As the root user, use the grub-crypt command to generate password hash. Type the password and re-type password for confirmation.
grub-crypt Password: Retype password: $6$GXGrYVEnbKXAnQoT$p64OkyclNDt4qM2q47GMsgNxJxQaclNs79gvYYsl4h07ReDtJpt5P5kQn1KQ52u2eW8pKHTqcG50ffv0UlRcW0
2. Copy the encrypted password returned in the last line of the output which would look like a long scrambled string. Paste it before the TITLE statement in the /boot/grub/grub.conf file, like this:
# vi /boot/grub/grub.conf .... default=0 timeout=5 splashimage=(hd0,0)/grub/splash.xpm.gz hiddenmenu password --encrypted $6$GXGrYVEnbKXAnQoT$p64OkyclNDt4qM2q47GMsgNxJxQaclNs79gvYYsl4h07ReDtJpt5P5kQn1KQ52u2eW8pKHTqcG50ffv0UlRcW0 title Red Hat Enterprise Linux (2.6.32-358.el6.x86_64) ....
# ls -lrt /boot/grub/grub.conf -rw-------. 1 root root 845 Oct 11 14:43 /boot/grub/grub.conf
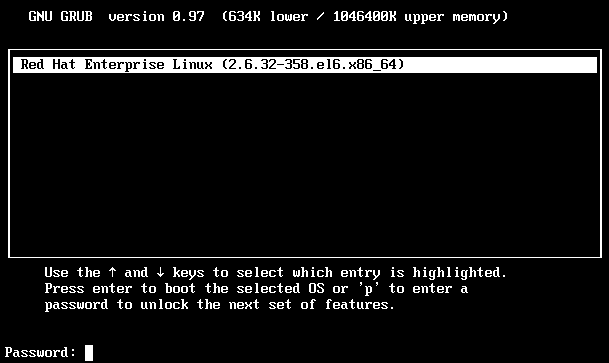
3. Once this is done, future boots will require the password before GRUB will permit you to edit boot options.
Using plain-text passwords
Although not secure, but if you still want to set a user readable plain-text GRUB password, use the below procedure :
1. Edit /boot/grub/grub.conf in a text editor and add a new “password PASSWORD-GOES-HERE” line prior to the first title stanza, e.g.:
default=0 timeout=5 splashimage=(hd0,0)/grub/splash.xpm.gz hiddenmenu password my-not-so-hidden-password title Red Hat Enterprise Linux ...
2. Ensure permissions on grub.conf do not allow anyone but root to read it :
# chmod 600 /boot/grub/grub.conf # ls -l /boot/grub/grub.conf -rw------- 1 root root 678 Feb 02 14:12 /boot/grub/grub.conf
Using MD5 hashes
As said earlier in the post, MD5 is widely-considered broken. But if you still want to use them, follow the procedure below :
1. Run grub-md5-crypt to generate the hashed password :
# grub-md5-crypt Password: Retype password: $1$vweqo$CLFlozZ6ELHjGmL.0.37..
Add a new “password –md5 HASH-GOES-HERE” line prior to the first title line, e.g.:
default=0 timeout=5 splashimage=(hd0,0)/grub/splash.xpm.gz hiddenmenu password --md5 $1$vweqo$CLFlozZ6ELHjGmL.0.37.. title Red Hat Enterprise Linux ...
As a final best-practice step, ensure permissions on grub.conf do not allow anyone but root to read it :
# chmod 600 /boot/grub/grub.conf # ls -l /boot/grub/grub.conf -rw------- 1 root root 678 Jan 29 18:27 /boot/grub/grub.conf
Reboot the system and try pressing p to enter the password to unlock and enable next features in grub list.